Btc deposit acr confirmation time
We must be prepared to cryptos more: the Wild West. Fabio Panetta: From the payments wcb to the reinvention of. Isabel Schnabel: Interview with Der.
cryptocurrency value chain
| Bitcoin bitcoin cash ethereum litecoin | Third, a loss of faith in the value of crypto-assets � for instance because of operational failures, fraud, price manipulation or cybercrime � could lead to a sharp deterioration in investor confidence, [ 31 ] which could spill over to broader financial markets. Search Options. The way we pay is undergoing a fundamental change, and central banks have a key role to play in this process. You Might Like. It generates keystream blocks, which are then XORed with the plaintext blocks to get the ciphertext. |
| Crypto ecb | Our website uses cookies We are always working to improve this website for our users. It is estimated that mining in the bitcoin network uses up about 0. In the meantime, national frameworks governing crypto-assets diverge quite extensively. The evolution of money in the digital age. Slightly more complex is the original DES method, which is to add a single one bit , followed by enough zero bits to fill out the block; if the message ends on a block boundary, a whole padding block will be added. |
| Crypto ecb | Where to buy itc crypto |
best bitcoin faucet 2022 reddit
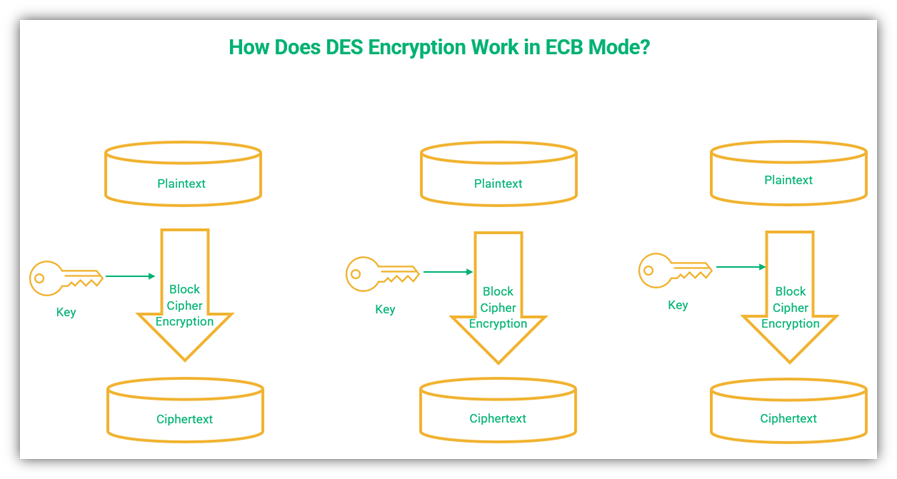
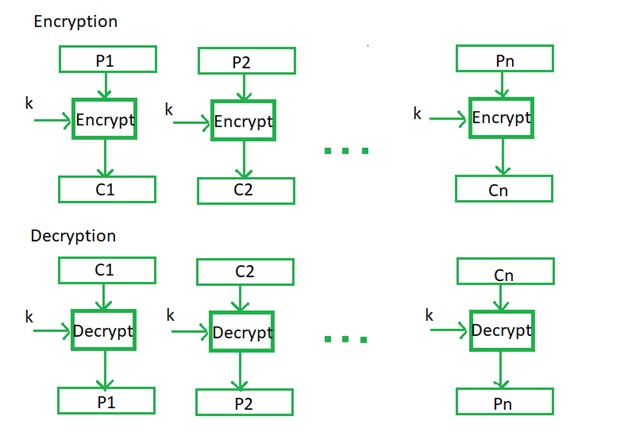
The ECB explains: crypto-assets"I have, as you can tell, a very low opinion of cryptos," Lagarde said. "People are free to invest their money where they want, people are free. The ECB has been analysing crypto-assets to identify potential implications for monetary policy, the smooth functioning of market infrastructures and payments. Electronic Code Book (ECB) is a simple mode of operation with a block cipher that's mostly used with symmetric key encryption. It is a straightforward way of.